On September 4th, my brother had $25,000 of assets drained from his Ledger wallet. I was perplexed.
After checking his transaction history, I found no interaction with a drainer, a malicious smart contract, or anything suspicious!
There was nothing.
After checking his transaction history, I found no interaction with a drainer, a malicious smart contract, or anything suspicious!
There was nothing.
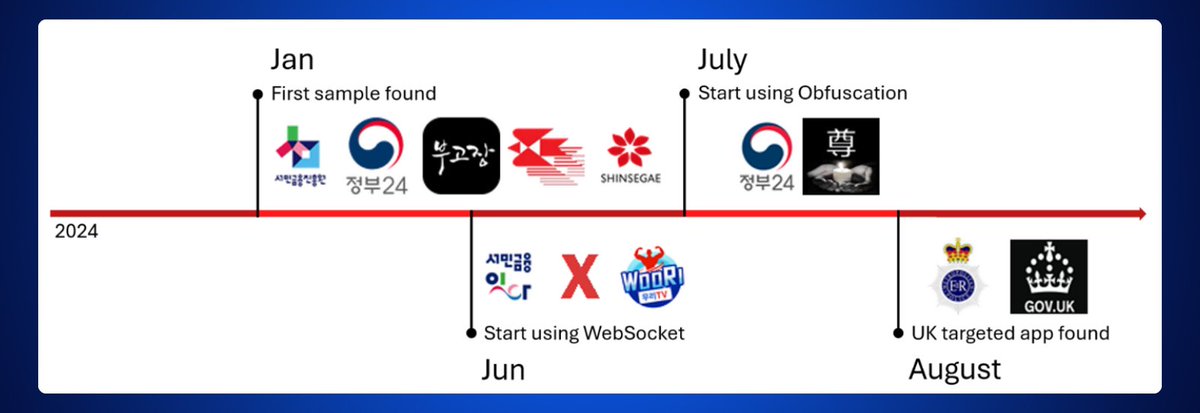
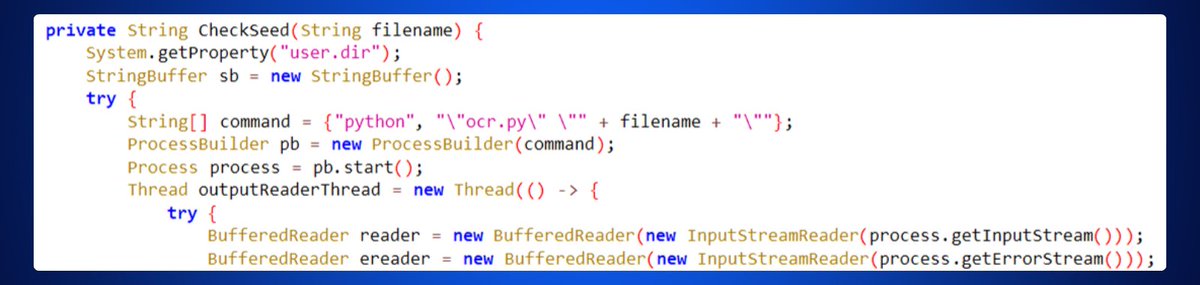
After running a full diagnostic on his phone, I discovered the presence of malware called SpyAgent.
This malware was hidden in a TV streaming app and had a very unique way of operating.
This malware was hidden in a TV streaming app and had a very unique way of operating.
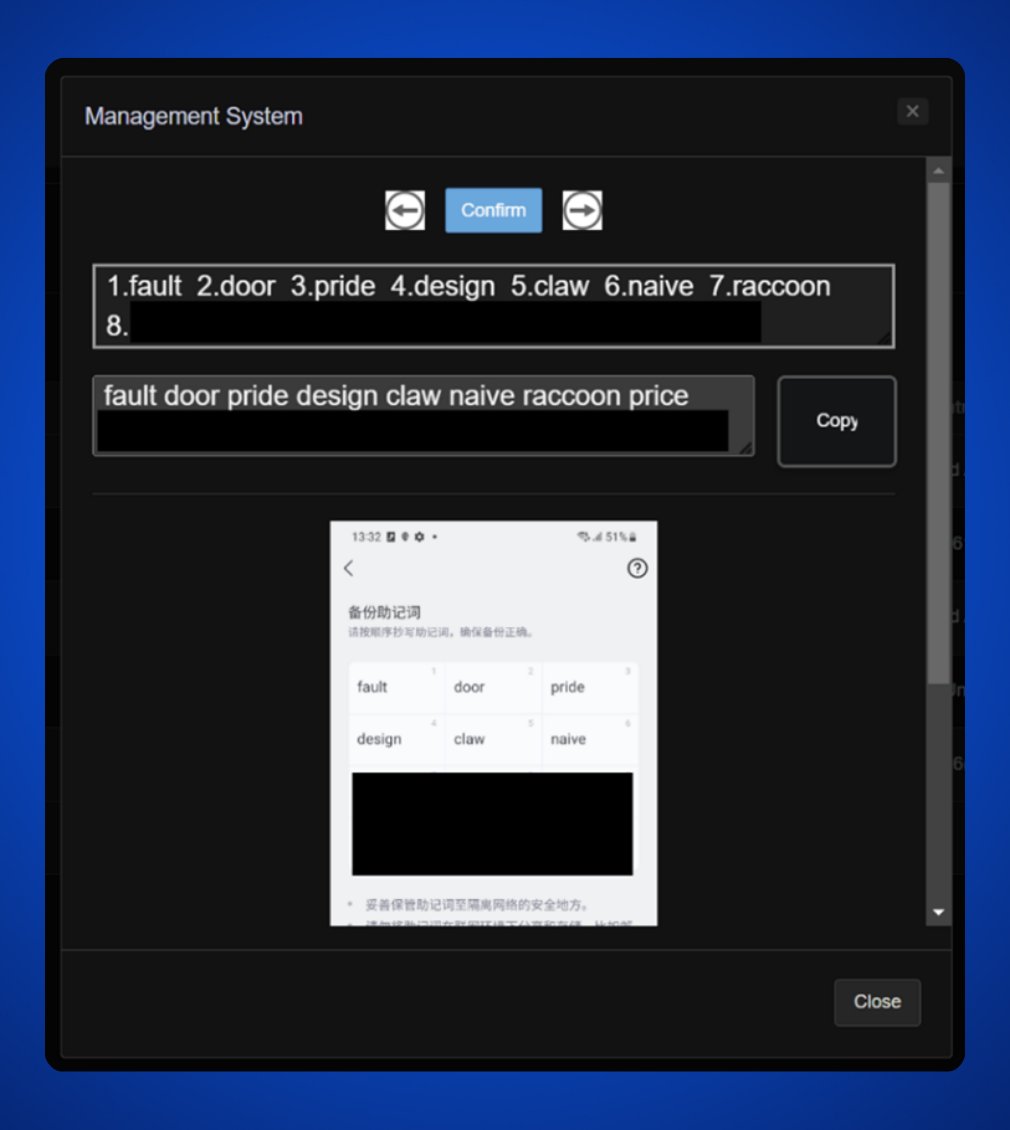
It scanned all the data on the phone, searching for patterns resembling a seed phrase.
What’s astonishing is that this malware could even recognize a seed phrase from a photo, even though it wasn’t in text form.
What’s astonishing is that this malware could even recognize a seed phrase from a photo, even though it wasn’t in text form.
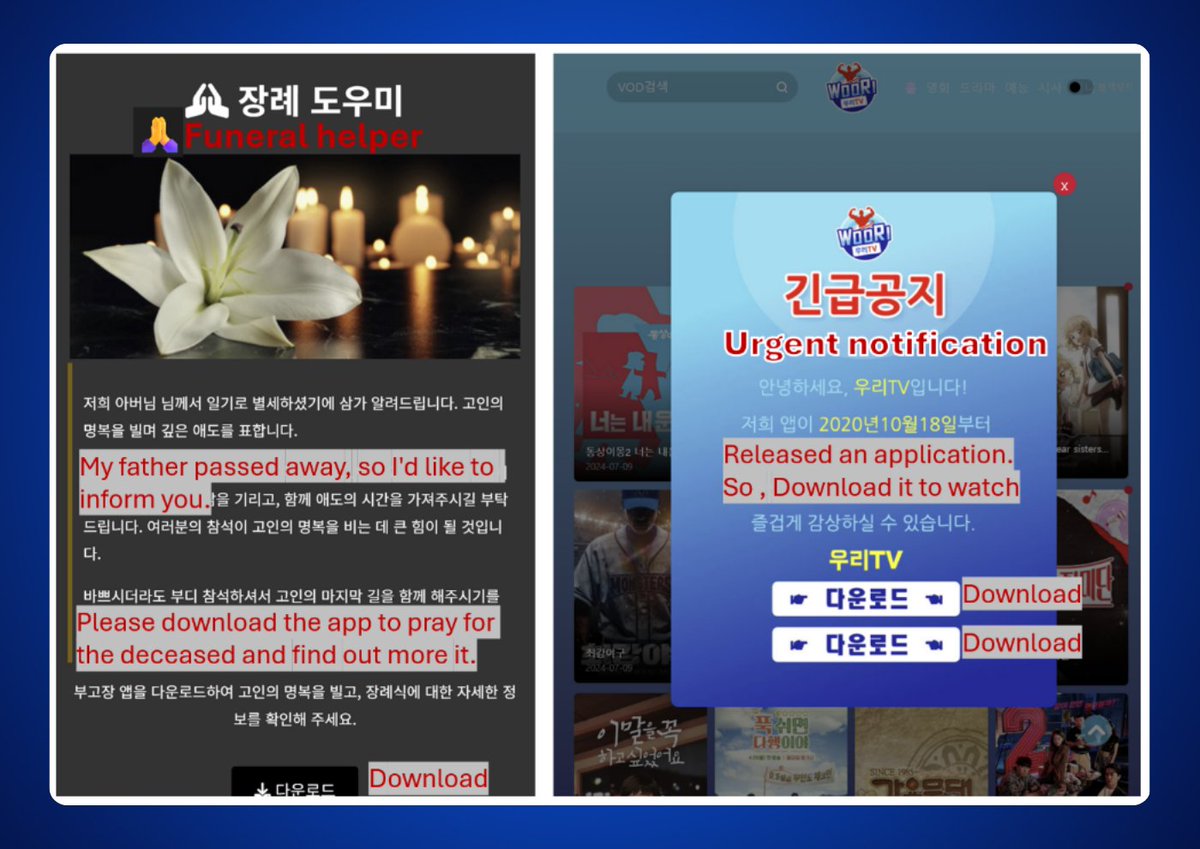
Mobile malware spreads through phishing campaigns using fake messages from trusted sources.
Once clicked, these links direct users to sites that imitate legitimate ones, tricking them into downloading malicious apps.
Always verify links before clicking! My brother got caught when he tried to download the X TV app.
Once clicked, these links direct users to sites that imitate legitimate ones, tricking them into downloading malicious apps.
Always verify links before clicking! My brother got caught when he tried to download the X TV app.
Once installed, the app steals sensitive data such as contacts, SMS, photos, and device details and sends them to a remote server.
It can also receive commands to manipulate settings, send SMS, and confirm data theft, compromising privacy and security.
It can also receive commands to manipulate settings, send SMS, and confirm data theft, compromising privacy and security.
The lesson?
Never store your seed phrase on any electronic device, even if it’s stored offline.
Whether it's a PC or a phone, there are now highly sophisticated hacks capable of detecting seed phrase patterns, even from a photo.
Never store your seed phrase on any electronic device, even if it’s stored offline.
Whether it's a PC or a phone, there are now highly sophisticated hacks capable of detecting seed phrase patterns, even from a photo.
I hope you've found this thread helpful.
Follow me @the_smart_ape for more.
Like/Repost the quote below if you can:
Follow me @the_smart_ape for more.
Like/Repost the quote below if you can:
Loading suggestions...