How to recognize scam coins?
While there are 101 ways to rugpull and scam people, I'm going to lay out one of the most obvious ways in this thead 🧵 Read on :-)
While there are 101 ways to rugpull and scam people, I'm going to lay out one of the most obvious ways in this thead 🧵 Read on :-)
First I used a quick #honeypot check on the page to see if the coin in question is buyable and sellable, it passed the test. It would be a big red flag 🚨 if this test failed, meaning the contract prevents selling the coin.
After I tend to open @DEXToolsApp, to quickly look if their are any trades happening. This is the page for the coin; dextools.io
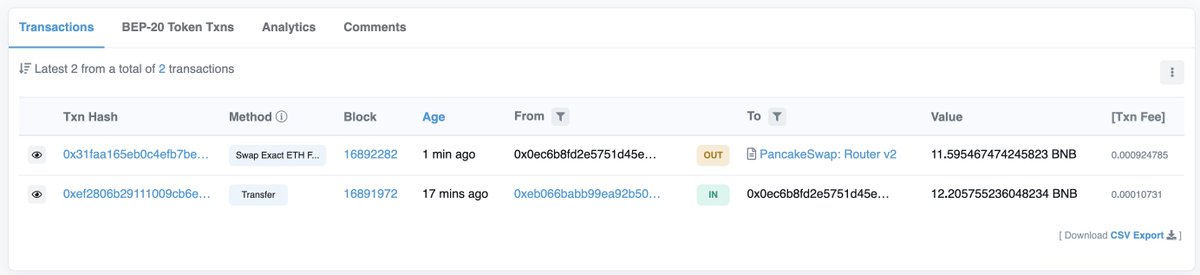
I spotted some pretty big buys early on, could be an indicator for a legit launch... or is it? 🧐
I spotted some pretty big buys early on, could be an indicator for a legit launch... or is it? 🧐
Clicking on the first two buyers' addresses:
bscscan.com
bscscan.com
I quickly noticed similarities, these were both brand new and funded from the same address, namely;
bscscan.com
bscscan.com
bscscan.com
I quickly noticed similarities, these were both brand new and funded from the same address, namely;
bscscan.com
This address first received many left-over BNB's from various temporary addresses, to then send it over to brand new one's to make the fake buys.
The final transfer, is a 63 BNB transfer to fund the initial liquidity (which is 100% burned);
bscscan.com
The final transfer, is a 63 BNB transfer to fund the initial liquidity (which is 100% burned);
bscscan.com
When you follow the money, you will encounter a rinse-and-repeat method of funding, collecting dust and refunding liquidity for the next scam coin. Happening 1 or 2 times per hour. Next to CATFORCE, you will see the previous coins CAMELCOIN, UNISALE, FUTUREDAO, and so on...
Two addresses seem to be outsiders, but luckily, they made very small buys (less than a dollar). Either they know or they only check for honeypots, but luckily this round no victims were made.
The turnaround time seems to be like ~34 minutes from token contract creation until the script sells all and drains liquidity and starts the game all over.
This scam only needs one person to #FOMO in and either the liquidity will be pulled immediately, or ...
This scam only needs one person to #FOMO in and either the liquidity will be pulled immediately, or ...
... just before the first real buyer tries to take profit. He would then be #frontrunned by the massive sell off.
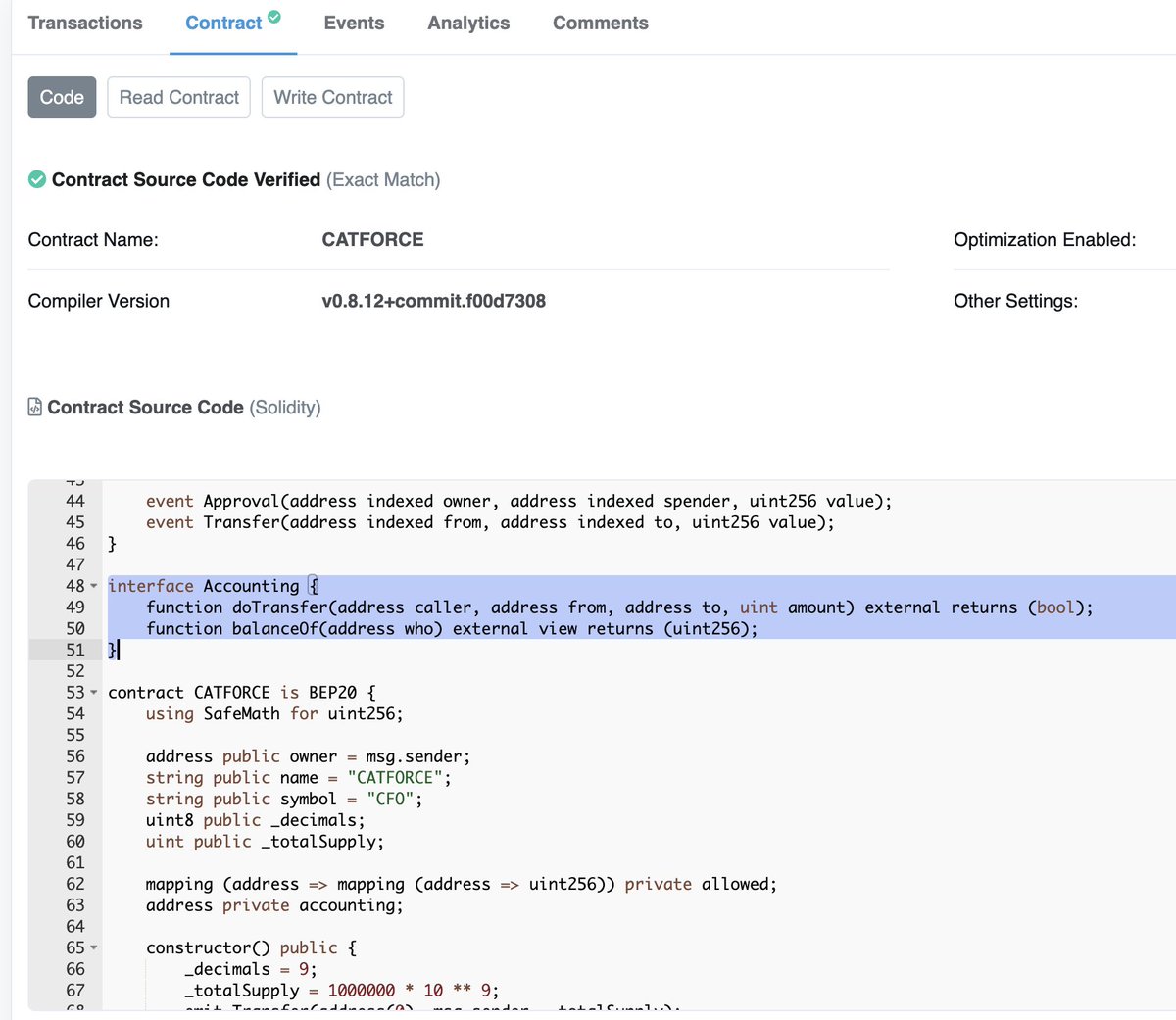
So how is the rugpull exactly performed? I'll explain!
So how is the rugpull exactly performed? I'll explain!
Besides this, the accounting contract also tampers with the 'transfer()' function by putting its own 'doTransfer()' function in between. This would never allow you to transfer coins to @PancakeSwap for making a decent sell with your tokens.
I hope this thread helps you understand at least one of the ways these scammers operate. Many green ticks are placed with this one, and still it's a scam.
✅ Verified contract
✅ Passes honeypot checks on various sites
✅ Burned coins
✅ Sufficient liquidity
✅ Locked (burned) liquidity
✅ Renounced ownership
✅ Big buys
✅ Decent volume
✅ Some successful sells
❌ Rugpull
✅ Passes honeypot checks on various sites
✅ Burned coins
✅ Sufficient liquidity
✅ Locked (burned) liquidity
✅ Renounced ownership
✅ Big buys
✅ Decent volume
✅ Some successful sells
❌ Rugpull
As said, this one is easily recognized when you click a few of the fake buys and you will see the same source of funding for these addresses. This can be disguised as well with just a little more advanced script! Always stay alert and never ape in too big. Stay safe friends!
Oh and beware... the next scam of this scammer is SquishiVerse (SLIME)
bscscan.com
Rugging in ~32 minutes...
Tag your friends to warn them for this scamming method!
bscscan.com
Rugging in ~32 minutes...
Tag your friends to warn them for this scamming method!
@themoontography I challenge you to recognize this scamming method and include it in @oklgio's Alpha as a Service
جاري تحميل الاقتراحات...