And the @awscloud re:Inforce livestream is up. SPONSORED BY PALO ALTO NETWORKS.
(No not this thread, because they lack imagination; the actual keynote livestream. It's *way* more expensive.)
(No not this thread, because they lack imagination; the actual keynote livestream. It's *way* more expensive.)
The EC2 15th birthday, some Twitch shows, re:Inforce, and the Americas Online Summit are all video options you can watch today, at largely the same times. Brought to you by @awscloud.
Amusingly, this is about how well the EC2 Instance Scheduler works, too.
Amusingly, this is about how well the EC2 Instance Scheduler works, too.
I think I'm the only person watching this, because when it comes to cloud security, @awscloud and I are apparently the only ones who give a shit.
For Amazonian color commentary, I'm corey@duckbillgroup.com on Chime. Not even slightly kidding.
Now let's see what this livestream has to say!
Now let's see what this livestream has to say!
And we start with @aselipsky.
"If security doesn't work, we don't have a business." It's nice to hear @aselipsky state it so directly. It's true.
"Please don't hesitate to tell us what you and your business need."
Suddenly @aselipsky realized that I'm watching this, and that he's just invited the vampire inside the house.
Suddenly @aselipsky realized that I'm watching this, and that he's just invited the vampire inside the house.
Next we have @StephenSchmidt. We can tell he's the CISO because of the dress code.
"Do you have the right demarcation between your work life and your home life?" asks @StephenSchmidt, briefly forgetting for which company he works.
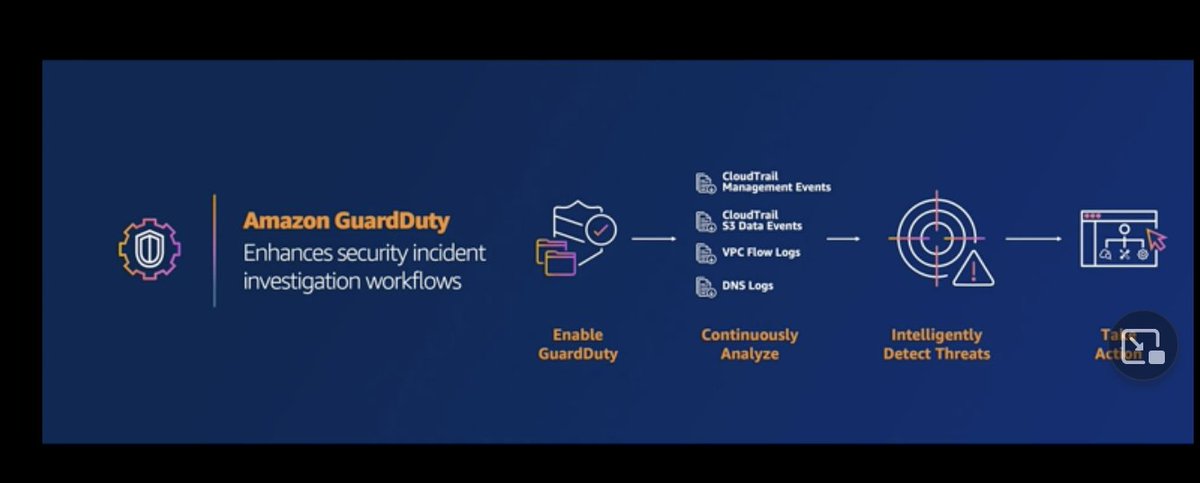
Talking about GuardDuty now.
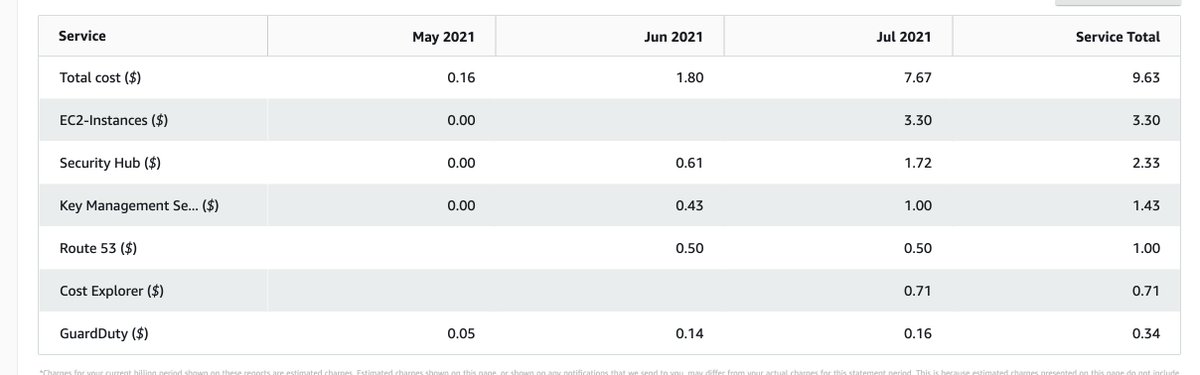
My hot take: it should be free. Otherwise it just feels like a cash grab, and doesn't compare super well to third party offerings.
My hot take: it should be free. Otherwise it just feels like a cash grab, and doesn't compare super well to third party offerings.
"There are some things you can only get with your provider's telemetry." Yeah, so why are you charging me for that?
You absolutely don't want security to be an investment decision, but of course there's an entire industry dedicated to ensuring it is and remains so.
Meanwhile over in my tiny shitposting account (seriously; it's got the coveted "shitposting" @awscloud account alias)
Now @StephenSchmidt is at the "car analogy" portion. "You don't want your airbag to deploy after the accident when it's safe, you want it to fire when it can help you during a crash."
Toyota files a protest.
Toyota files a protest.
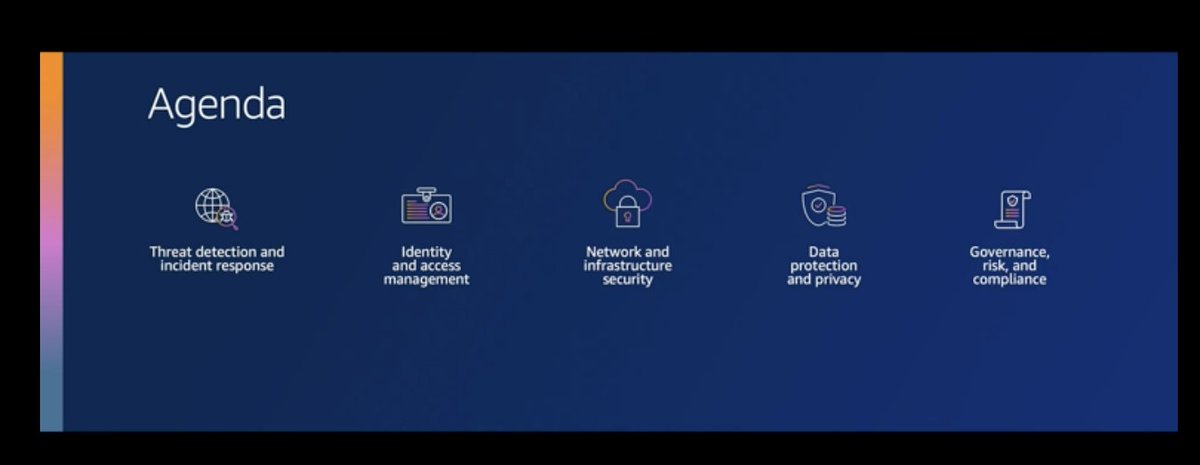
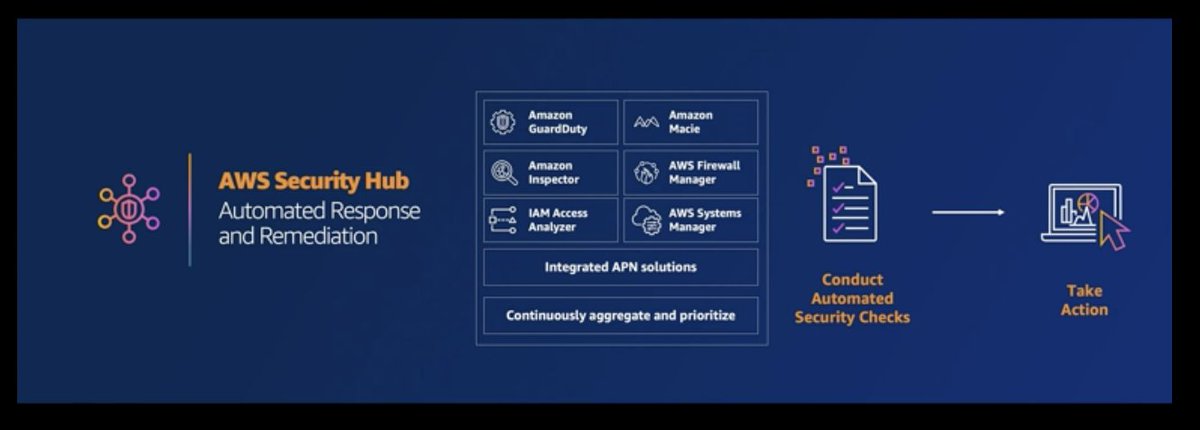
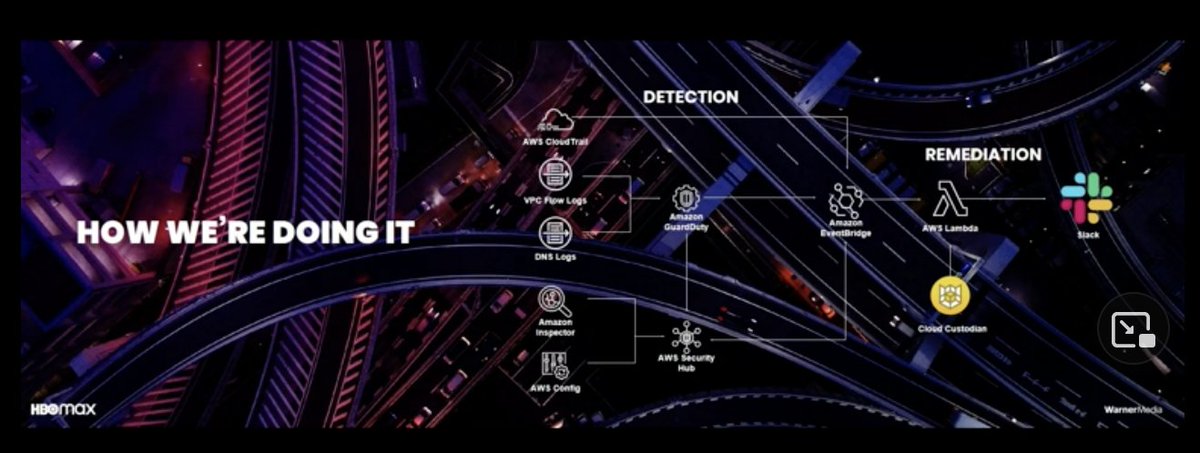
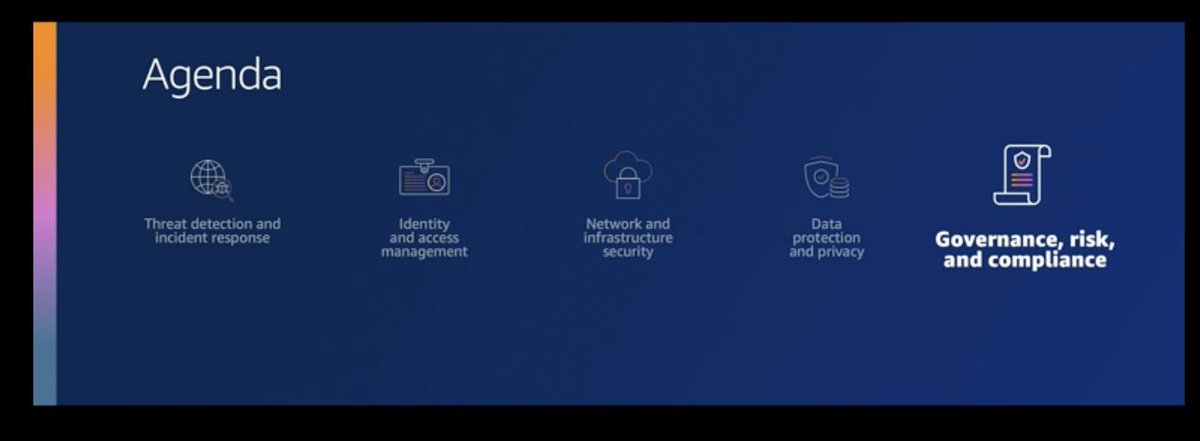
CloudTrail, GuardDuty, Flow Logs, Security Hub. Which does which?
I point out that @StephenSchmidt used the phrase "deploy with a single click" a few minutes ago.
I point out that @StephenSchmidt used the phrase "deploy with a single click" a few minutes ago.
Telling the story about someone who needed access so they were deployed with admin perms so things wouldn't get in the way, as if this were a bizarre thing that no one sensible would ever do it.
Buddy, I've got Lambda functions, EC2 instances, and a CodeBuild role like that.
Buddy, I've got Lambda functions, EC2 instances, and a CodeBuild role like that.
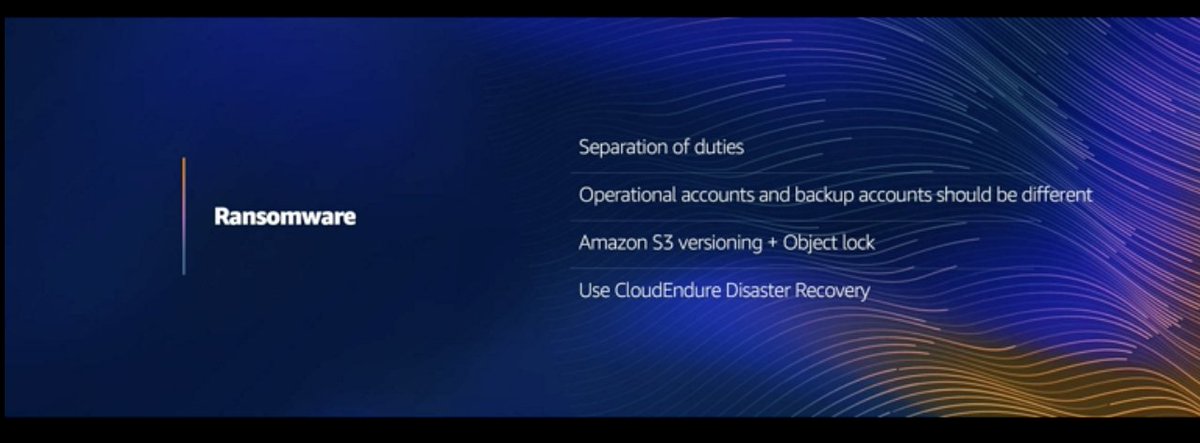
"If you pay us, you get access to your data again. If you don't, you can't."
@StephenSchmidt describing the ransomware / cloud billing model.
@StephenSchmidt describing the ransomware / cloud billing model.
"I also want to mention CloudEndure, because we didn't spend $200m to acquire it for me to *NOT* talk about it, y'know?"
More info on this is available at aws.amazon.com
"We expect cyber insurers to require this level of rigor." Ah, there's the stick!
"What if your commonly used password gets leaked?"
We've tried for decades to get people to use different passwords and it hasn't worked. I wonder if "passwords must include one slur" would make people treat them more seriously, because nobody wants THAT to leak!
We've tried for decades to get people to use different passwords and it hasn't worked. I wonder if "passwords must include one slur" would make people treat them more seriously, because nobody wants THAT to leak!
Holy hell @StephenSchmidt just pointed out that IAM is free. I'm trying to imagine a billing model for it and just blacked out for a second.
Hell yes he just referenced "Des Moines, Iowa" as an example of a faraway place. I did a project there once. He is correctd.
Talks about "wondering if someone who's left the company holds a grudge."
An @awscloud database service team salivates about how much money they'd make keeping a list of various parties who hold grudges. TO THE PR FAQ GENERATOR!
An @awscloud database service team salivates about how much money they'd make keeping a list of various parties who hold grudges. TO THE PR FAQ GENERATOR!
(If you want a serious, less shitposty version of this, @marknca is absolutely worth following.)
Now @StephenSchmidt talks about a new vertical. Meanwhile it's so early that many of us are still horizontal. Read the room!
And almost without realizing it, @ajassy has stepped from the stages of re:Invent into the pages of history. He's now a mythic figure that gets quoted instead of invited.
Not kidding. There's a non-zero chance that my shitpost actually inspired it.
Fascinating observation: AWS used to talk about "the cloud." Now @StephenSchmidt is talking about "our cloud."
Sidebar: This is why I do "Cost Optimization," not "Cost Reduction." You'd save money by turning all of this stuff off but you absolutely shouldn't do it.
"Everyone here is an automation away from updating their résumé." Now that's a bold thing for a tech leader to say. I approve!
"Anything worth doing is on the other side of hard." My god, this guy's a walking quotation source. I just want to make him wear a wire for an afternoon and come up with my next sixty blog posts.
And he ends with a video. It's a bunch of clips from HBO movies. Good use of back catalog assets there.
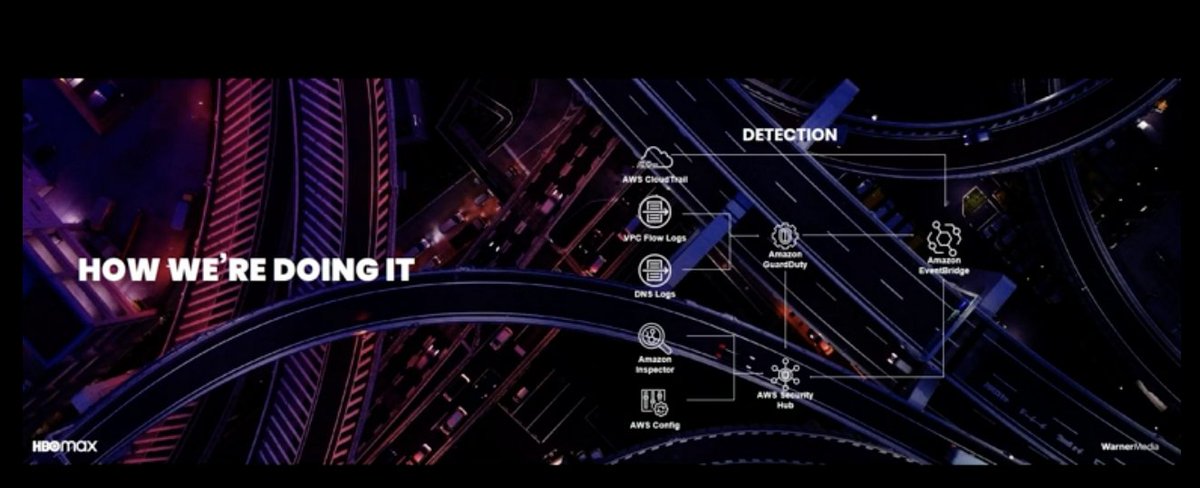
And back to @StephenSchmidt who awkwardly segues with a reference to some HBO Max show I've never heard of.
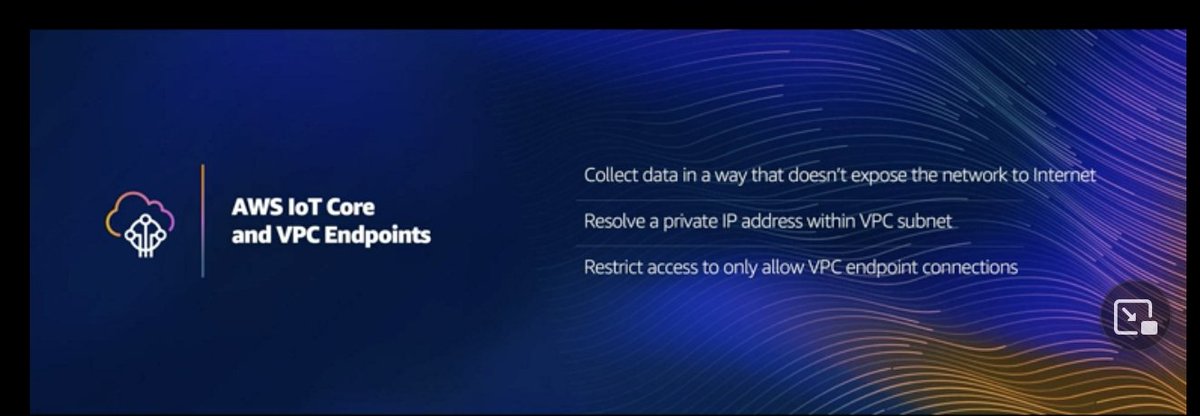
...and now @StephenSchmidt wanders into the fantasy land of "Confidential Computing." Ugh.
Look, either you trust your provider or you don't and shouldn't use them.
Look, either you trust your provider or you don't and shouldn't use them.
And he pivots to "not trusting your own staff," which is a super key differentiator. I may not want my admins to have access to my app data / secrets. That wasn't really possible back in my admin days; we solved for it by heavy auditing and "you're fired if you read that data."
Now talks about the Well Architected Tool. It's not really any of those three things.
Apparently the @awscloud internal culture is shifting to Hunger Games inspired approaches.
Now @StephenSchmidt demonstrates how cutting edge the team is. It used to be you weren't allowed to sponsor @RSAConference without the word "Firewall" in your product. These days it's "Zero Trust" and he's talking about it now.
Hahahah now he references that 'Zero Trust' is a marketing term that means nothing. Okay, I admit it. I like @StephenSchmidt.
Whoa whoa whoa. @StephenSchmidt just said "that's a mouthful, thanks lawyers."
YOU WORK AT AWS! You get to cast exactly ZERO shade about crappy terms of art / names!
YOU WORK AT AWS! You get to cast exactly ZERO shade about crappy terms of art / names!
Right?! There's a *reason* I know basically "what's your email address" and nothing else about @LastWeekinAWS subscribers.
(I'm told that the HBO Max CISO is @BrianL1775 and oh no he follows me)
I see @werner's t-shirt has been turned into an Enterprise Slide.
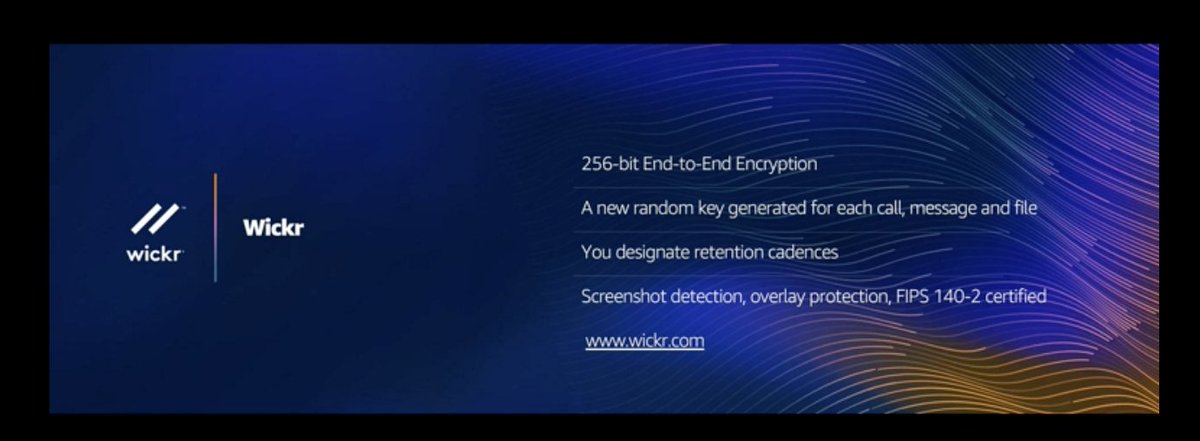
"We acquired Wickr earlier this year. Please do not call me 'The Wickr Man.'" --@StephenSchmidt, if I wrote his slides for him
I adore @AnnaKendrick47 as much as anyone, but this metaphor was tortured so much that Amnesty International is getting involved.
Now it's "words from our sponsors." They're not *my* sponsors (and my twitter feed is never sponsored), so I won't be repeating their messages here. They (and you!) can contact sponsorships at lastweekinaws.com if they want to talk about fun messaging options!
Or, y'know. Just ask @CarolineVCarter because she's awesome at this.
Internal program at @awscloud. People who sit outside of the security org, but enforce security practices in their own org.
Interesting. More details to come at re:Invent.
Interesting. More details to come at re:Invent.
Ooh, it counts as continuing education credits. If you need those, you know.
What the hell, @StephenSchmidt forgot to include my Twitter account on the slide!
And that ends the (surprisingly fun!) keynote. Thanks for following along with my Twitter nonsense. As always, lastweekinaws.com is where my newsletter signup lives if you'd like to get this kind of nonsense in your inbox weekly.
Loading suggestions...